OpenID Connect - OIDC
Settings on the OpenID Connect (OIDC) tab (pictured below) specify the configuration that allows the On-Premise License Server to access information stored in the authentication server.
The On-Premise License Manager implements the authorization code flow and needs to obtain client id and client secret so users can log in with the OIDC identity provider (IDP).
Note
The License Manager must be configured as an application on the OIDC identity provider (IDP) side, for example, Okta. Use the callback URL displayed in the OIDC settings as the redirect URI.
client ID and client secret are unique identifiers that will be used to authenticate the On-Premise License Manager with your OIDC server.
By configuring OIDC:
License administrators can assign license seats to users by users’ names.
Your teammates can log into the Licensing Portal using their OIDC credentials.
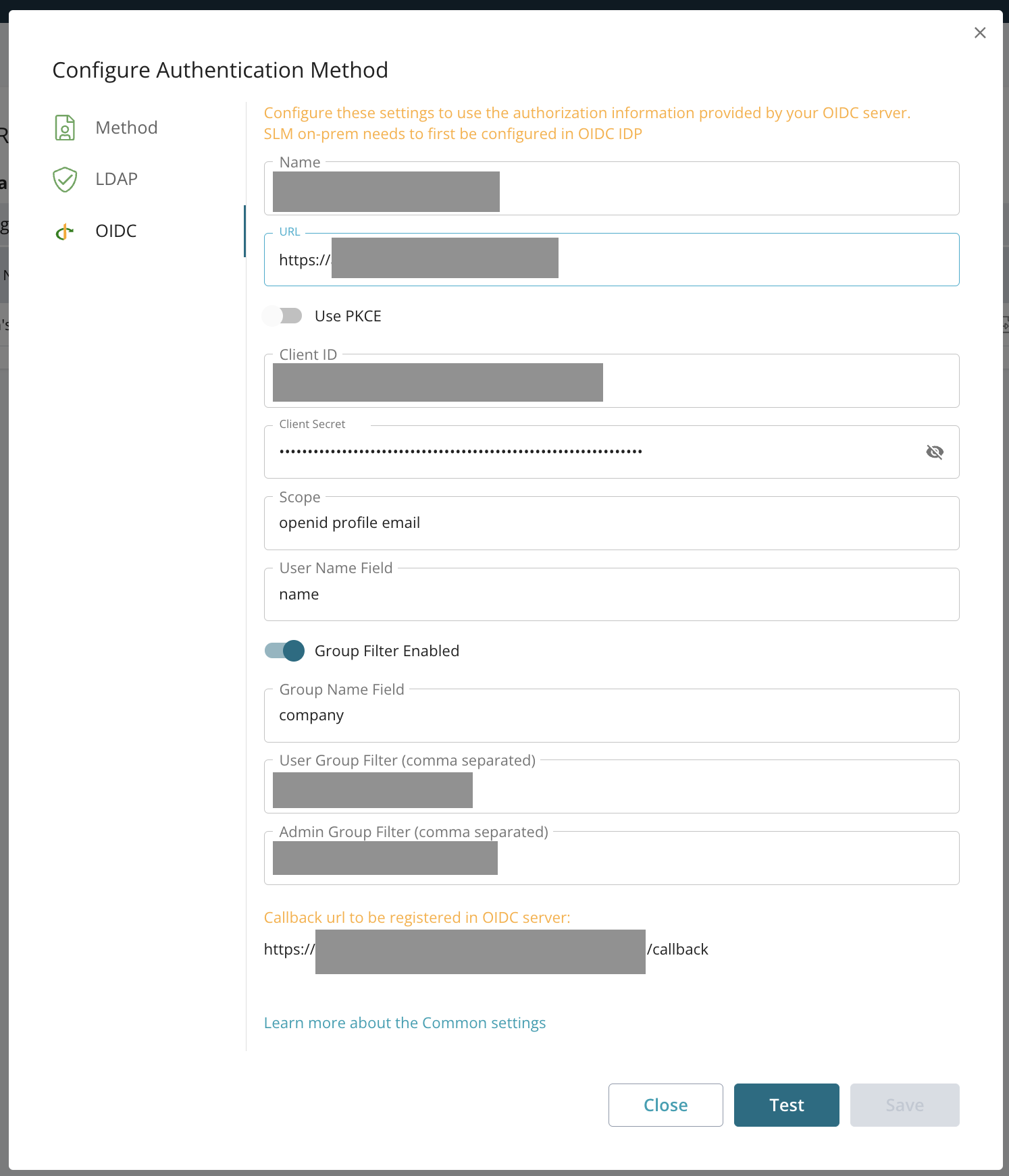 |
Here are definitions for the values requested in the configuration fields:
Field | Description |
|---|---|
Name | Descriptive name of the configuration |
URL | OIDC server URL |
Use PKCE | Toggle the switch to use the PKCE-enhanced Authorization Code Flow. For more information, see Authorization Code Flow with Proof Key for Code Exchange (PKCE) from Okta. |
Client ID | Unique identifier for the On-Premise License Manager on the OIDC server |
Client secret | Unique string paired with the Client ID value for the On-Premise License Manager on the OIDC server |
Scope | Scopes are permissions that your application will need to access user data. You will need to add openid, profile. In some environments, the email scope will also be required. The OIDC server will only grant the scopes that you have requested. |
User Name | Field in the token that contains user data. This depends on you OIDC server configuration. Common fields for storing user data in OIDC tokens include email and name. |
Group Filter Enabled | Toggle the switch to use group filtering and manage access control based on the group membership. |
Group Name Field | Field in the token that contains group data, for example, company or department |
User Group Filter | To grant permissions to resources, add values configured on the OIDC server that match the client's requirements. |
Admin Group Filter | To grant administrator permission, add values configured on the OIDC server that will assign elevated scopes. |
Callback URL to be registered on the OIDC server | Use this URL as the redirect URI in the OIDC server settings. |
Note
The filters in OIDC settings apply only to users authenticated via the OIDC server. Service accounts do not have groups assigned.
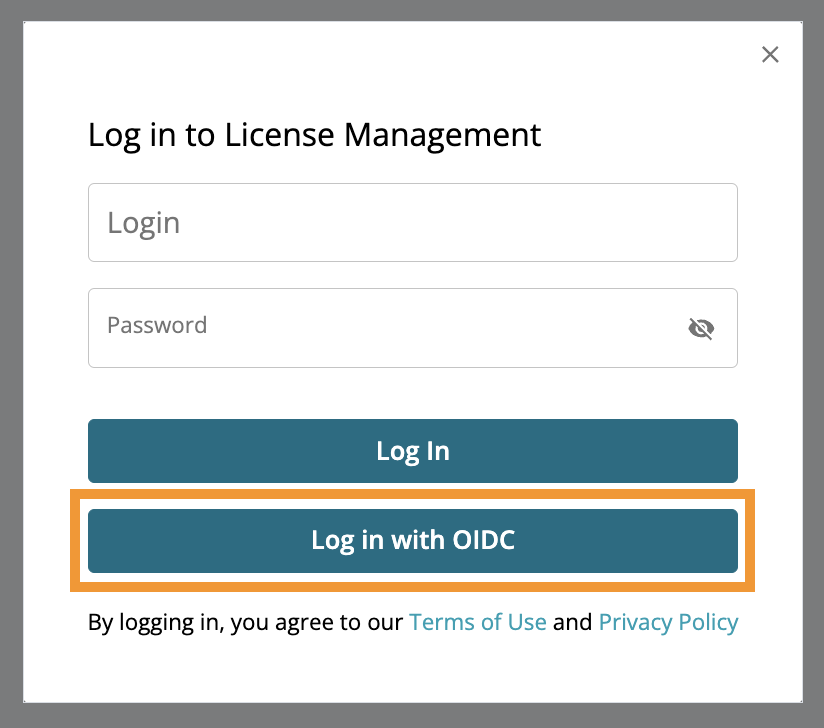
Test your configuration.
After configuring the OIDC method, the button shows on the login page. Users must use this button to log in.
 |
For more information on Open Connect ID, see How Open ID Connect Works.